Resources
All documents

Quantitative risk assessment using the Surface method
White paper ⋮ March 2025
Structured, reproducible, objective and verifiable is Circle Networks' numerical risk assessment for continuous system monitoring and development support.
Running you own mail server II: Cyrus IMAP
Blog post ⋮ December 2024
Securely running your own mail server isn't hard with the right software. Cyrus IMAP is a straightforward mail box server and the perfect companion to OpenSMTPD.
Running you own mail server I: OpenSMTPD
Blog post ⋮ December 2024
Securely running your own mail server isn't hard with the right software. OpenSMTPD offers all you need without complexity. Set up within minutes, it hardly leaves room for any mistakes.

Web application software licence
Licence ⋮ April 2024
Commercial end-user licence for the proprietary software in our web applications.

Quantitative risk assessment using the Surface method
White paper ⋮ April 2024
Structured, reproducible, objective and verifiable is Circle Networks' numerical risk assessment for continuous system monitoring and development support.

Appliance software licence
Licence ⋮ March 2024
Commercial end-user licence for the proprietary software on our appliances.

Sustainable software development using C
White paper ⋮ December 2023
The programming language C is more than half a century old. Yet, it is unbeatable when it comes to sustainability, both in terms of the environment, and for formal development of security critical systems.

How to merge: the overlooked key to a good git strategy
Blog post ⋮ January 2023
Amid debates on the optimal git strategy, an important aspect is often overlooked. It is not the strategy that determines the maintainability of your repository, but the way you handle your merges.
Axing the leap second is not science — it is a defeat against it
Blog post ⋮ November 2022
After years of debate, leap seconds will be abandoned as of 2035. The decision calls for science to come up with a solution, where in fact, it is a total defeat - in order to protect an obsolete Unix design.
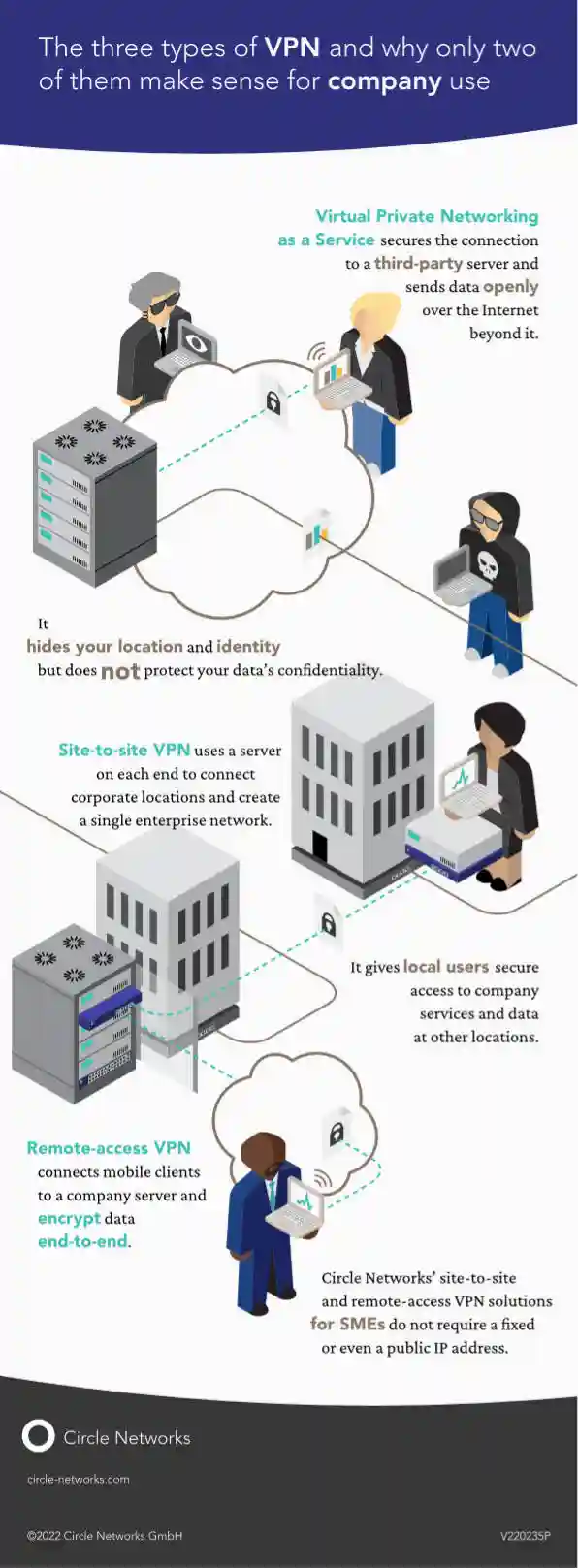
Three types of VPN and why only two of them make sense for company use
Infographic ⋮ October 2022
VPN is a generic label for several different use cases, in which data in transit on the Internet are protected by a tunnel. Three main types exists that should not be mixed up.
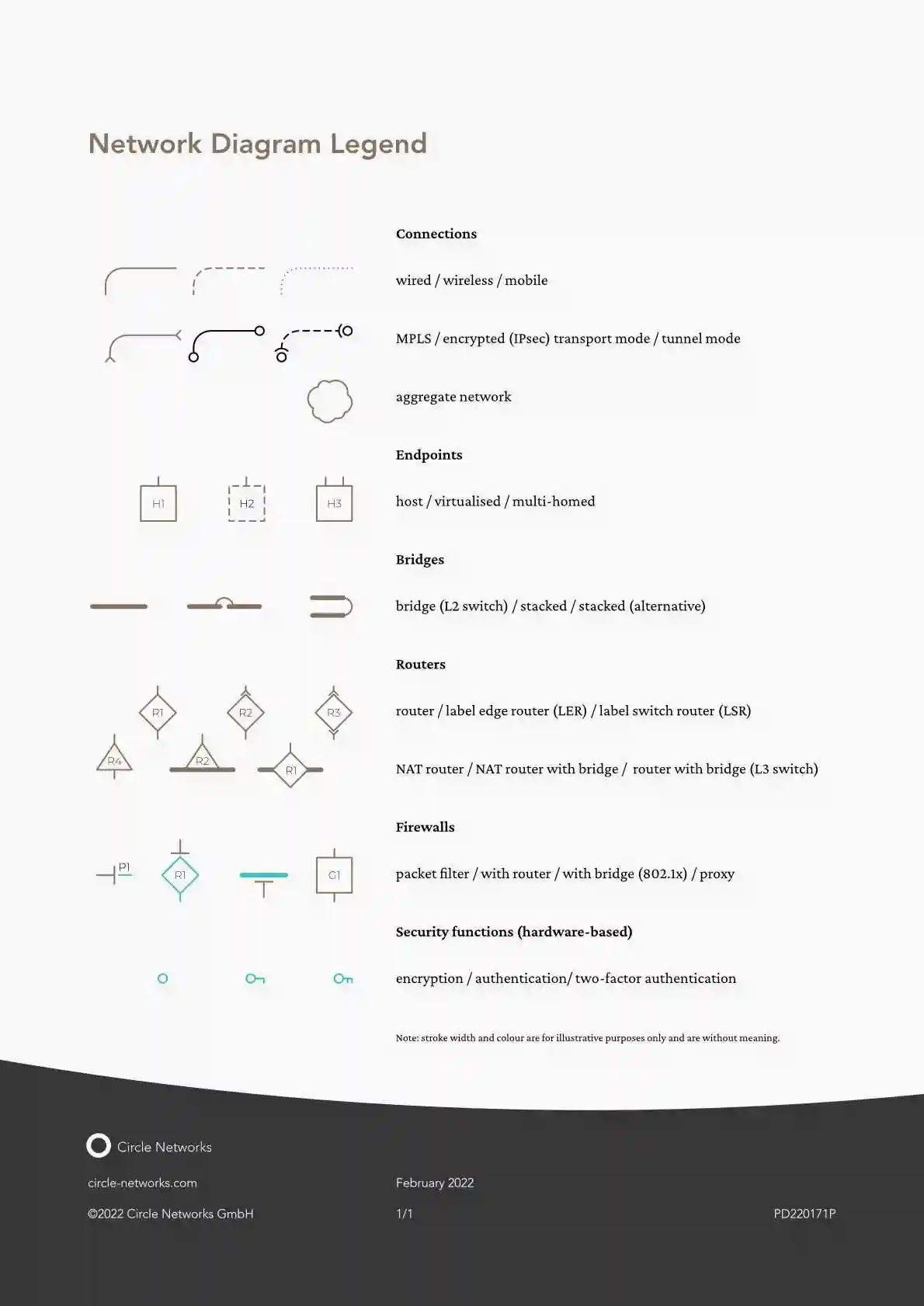
Network diagram legend
Data sheet ⋮ February 2022
Overview of network diagram symbols with meaning and proposed annotations.
Insecurity by transparency
Blog post ⋮ February 2022
Publishing security fixes on open-source platforms creates an opportunity for attackers to exploit the underlying vulnerabilities, which exceeds the usual case of not-yet-patched systems.

Network diagram legend
Data sheet ⋮ January 2022
Overview of network diagram symbols with meaning and proposed annotations.

Standardised symbology for network diagrams
White paper ⋮ January 2022
Every technical disciplin has its own standardised symbology — only network technology so far does not. Circle Networks thus introduced uniform symbols for network diagrams.
Configuring StrongSwan through swanctl.conf
Blog post ⋮ November 2021
StrongSwan's new configuration file, swanctl.conf, introduces clearer terminology and thus simplifies setting up remote access.

Attack surfaces and attack vectors
White paper ⋮ October 2021
What is an attack vector? What is the attack surface and is it necessary, to keep it as small as possible? There are many contradictory answers. Circle Networks uses simple and practical definitions for both.

Assessing IT security risks
White paper ⋮ August 2021
The assessment of IT security risks is often complicated and many models are contradictory. Circle Networks' risk assessment model uses simple terminology and helps to practically rank risks.
Sending and processing ARP requests/responses using BPF (updated)
Blog post ⋮ November 2020
Being between layers 2 and 3, ARP is handled by the operating system; but it can be useful to control ARP for checking ARP cache validity or finding hosts. BPF allows you to do so on BSD systems.

Secure networks for small enterprises
Video ⋮ November 2020
Every fourth small enterprise has no form of cyberprotection. The root problem is the lack of security at the network level. Our value proposition in 45 seconds.
Prevent your OpenBSD shared-memory objects from being axed by daily(8)
Blog post ⋮ June 2020
The temporary files that underly shared-memory objects will be destroyed by system maintenance after a week, unless you update file times to prevent this.
Building an OpenBSD VPN server with iked and OpenSSL
Blog post ⋮ April 2020
OpenBSD comes with a great IKEv2 server: iked. But the front-end ikectl has its limitations. It is easy to run iked with the underlying OpenSSL directly.
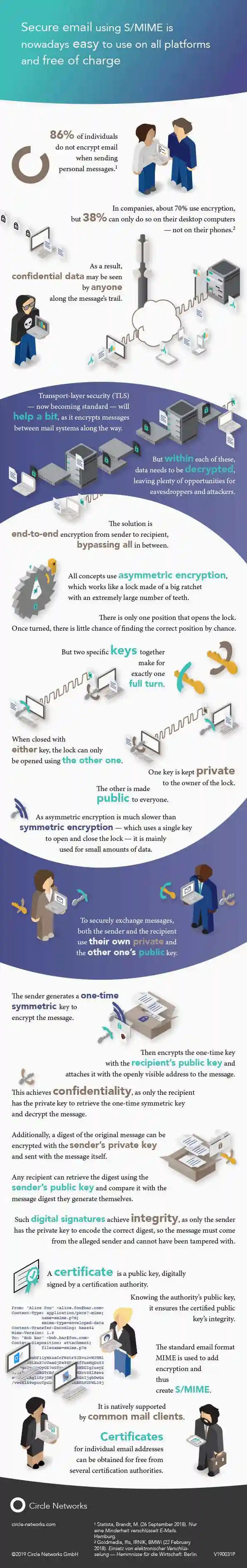
Secure email using S/MIME is nowadays easy to use on all platforms and free of charge
Infographic ⋮ February 2019
Still, only a minority encrypts its email, although the process to do so is natively supported by all common email clients. It does not require much to understand how to send email confidentially and how to ensure, that incoming messages are real.
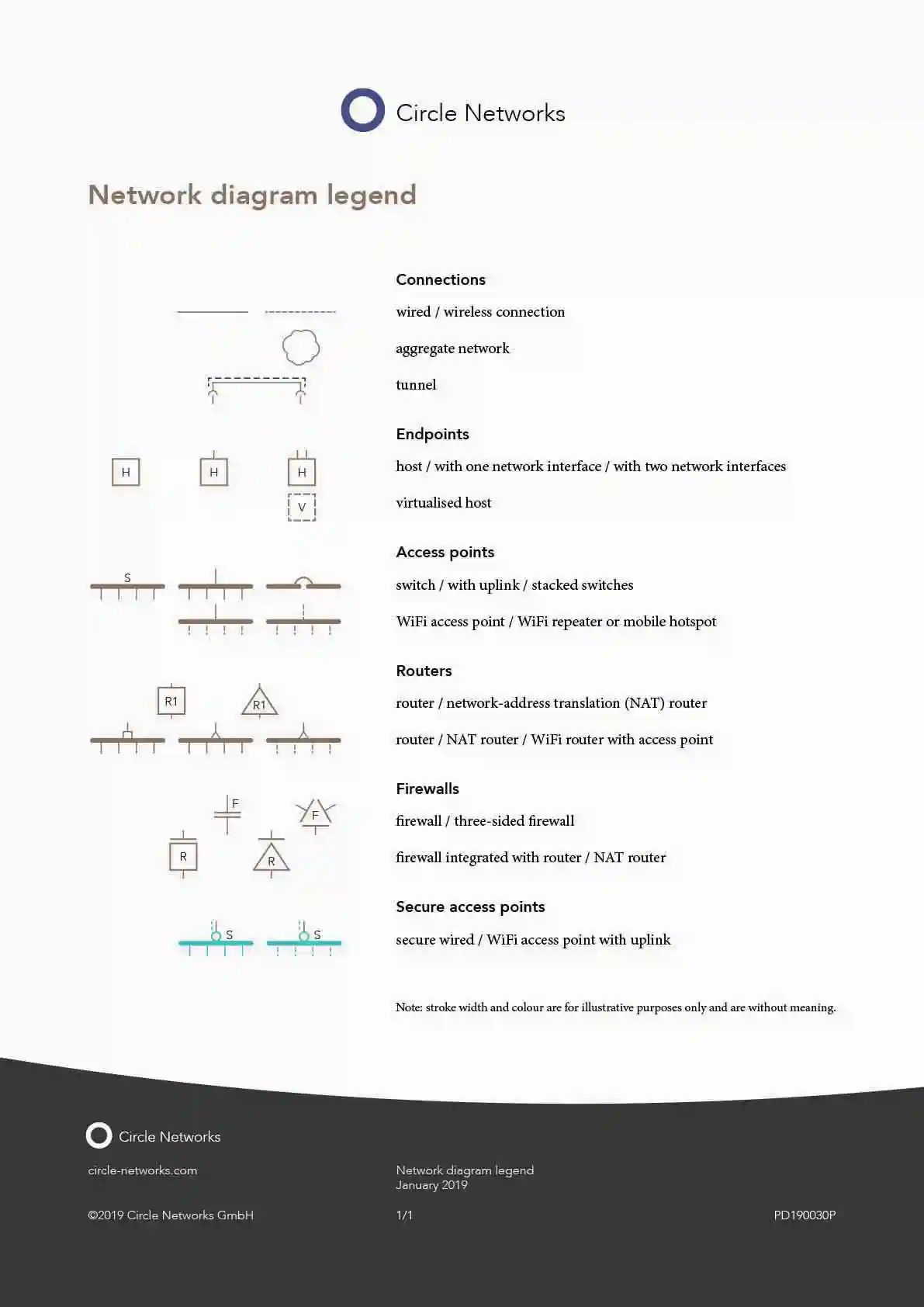
Network diagram legend
Data sheet ⋮ January 2019
Overview of network diagram symbols with meaning and proposed annotations.

Standardised symbology for network diagrams
White paper ⋮ January 2019
Every technical disciplin has its own standardised symbology — only network technology so far does not. Circle Networks now introduces uniform symbols for network diagrams.
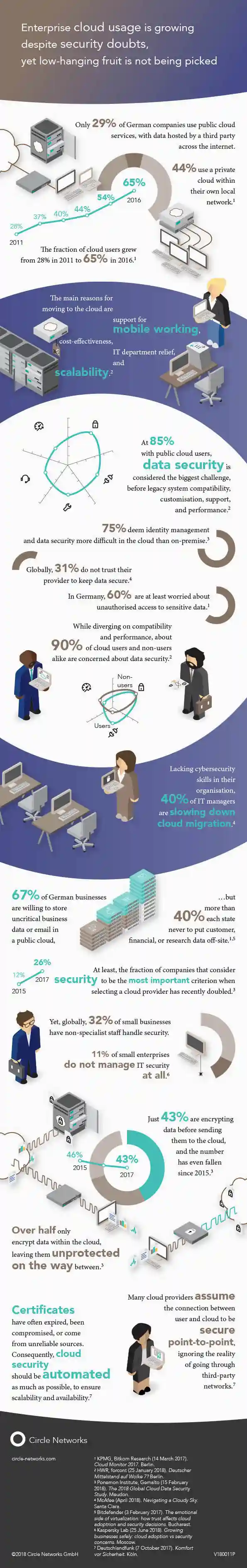
Enterprise cloud usage is growing despite security doubts, yet low-hanging fruit is not being picked
Infographic ⋮ October 2018
Companies expect the cloud to increase flexibility and to reduce cost. Security however is a reason for concern and is blocking a larger proliferation. There are simple measures, but often enough, they are not applied.
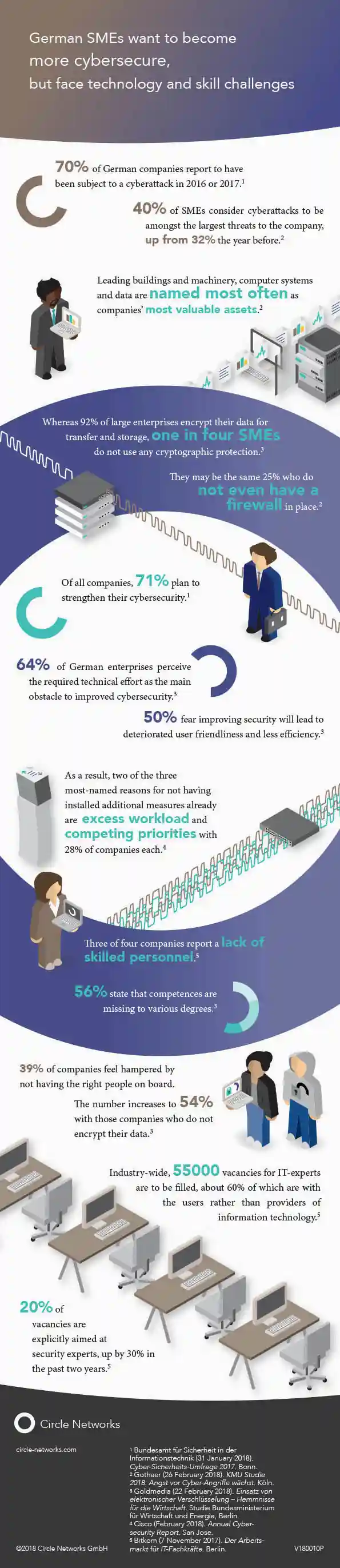
German SMEs want to become more cybersecure, but face technology and skill challenges
Infographic ⋮ April 2018
Small and medium-sized enterprises in Germany are generally aware of the risks of cybercrime, but many have little or no security measures in place. There is a clear correlation with the difficulty to find the right people.